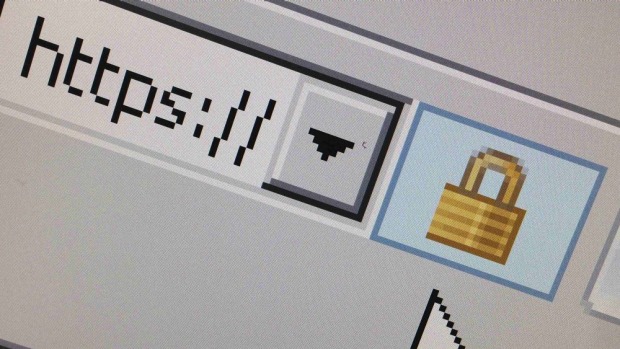
A new security vulnerability has been found that is bigger than Heartbleed. Photo: Reuters
A new security vulnerability found in web servers, computers and internet-connected devices such as light bulbs, web cameras, thermostats and industrial control systems has leading security experts warning it is worse than Heartbleed, the bug found earlier this year that affected almost every device.
Dubbed “shell shock”, the new bug enables hackers to exploit a vulnerability in “Bash”, the Unix shell used by millions of devices across the internet, including Apple laptops, desktops and phones.
A Unix shell enables computer users to issue commands to an operating system. Typical users have no need for access to shell but system administrators and others do.
“This is likely the largest ever attack vector surface for any bug, ever,” Australian security consultant Nik Cubrilovic said.
“Bash just happens to be one of the small number of applications that is integrated absolutely everywhere: from web servers, mail servers and remote administration servers through to Android phones, embedded devices and appliances.”
An attack vector surface is the sum of the different points – the “attack vectors” – where a hacker can try to extract data using a vulnerability from an environment.
Speaking from the US, Robert Graham, a security consultant at Errata Security who has been monitoring the bug, told Fairfax Media its potential impact was worse than Heartbleed.
Mr Graham said there was not much consumers could do but ensure their home router’s firewall was correctly configured to stop hackers exploiting vulnerable devices on their network.
He urged system administrators of servers which host websites to update their security as soon as possible to ensure data was not stolen by hackers who he expected are actively exploiting the new-found bug.
Mr Cubrilovic said the bug was taking up his entire day with clients needing fixes.
“It has me in incident response mode with a number of the companies I work with,” he said.
“[It] took some explaining as to why patching bash on all servers is so urgent – since most people associate bugs in Bash with local exploits, and don’t immediately see the remote exploit vector.”
As the bug allowed remote command execution, it was “the worst class of bug”, Cubrilovic said.
He urged administrators to upgrade their servers and devices immediately.
“Update bash immediately, or remove it and replace it with another shell,” he recommended. Administrators should also monitor their web server and system logs for any strange requests.
Tod Beardsley, an engineering manager at cybersecurity firm Rapid7, warned the bug was rated a “10” for severity, meaning it has maximum impact, and rated “low” for complexity of exploitation, meaning it is relatively easy for hackers to launch attacks.
“Using this vulnerability, attackers can potentially take over the operating system, access confidential information, make changes, et cetera,” Beardsley said. “Anybody with systems using Bash needs to deploy the patch immediately.”
Ty Miller, managing director of Sydney-based Threat Intelligence, said initial research indicated that the vulnerability was highly likely to be wide spread and had the potential to be more damaging than Heartbleed.
He said it allowed affected operating systems to become totally compromised, “providing the attacker with a foothold on the internal network of the victim”.
“If the victim is an organisation, then attackers are able to escalate their privileges and take over the organisations systems within a day and lead to large scale data theft,” Miller said.
The US Department of Homeland Security’s United States Computer Emergency Readiness Team, or US-CERT, issued an alert about the bug . It said Apple’s latest desktop and laptop operating system, OS X 10.9.5, was vulnerable, as well as many other Linux-based systems.
US-CERT advised computer users to obtain operating systems updates from software makers. It said that Linux providers including Red Hat had already prepared them, but it did not mention an update for OS X. Apple representatives could not be reached.
Australian security consultant Chris Gatford, of HackLabs, said the bug would result in “another long couple of weeks for system administrators and another useful exploit to use for next three years”.
Mr Miller agreed. “We are likely to find that this vulnerability will be exploitable on a significant portion of the internet and will be for a long time,” he said.
Mr Graham said many devices would probably remain vulnerable forever as some firms that have made internet-connected devices may have shutdown or may not be supporting old devices affected.
“Heartbleed”, discovered in April, is a bug in an open-source encryption software called OpenSSL. The bug put the data of millions of people at risk as OpenSSL is used in about two-thirds of all websites. It also forced dozens of technology companies to issue security patches for hundreds of products that use OpenSSL.
It was found being actively exploited in the wild, with one Canadian teen arrested for stealing tax information from the Canada Revenue Agency website.
Follow IT Pro on Twitter
With Reuters